
|
Читайте также: |
Cache Design
Size (more optimal size: between 1K and 512K)
Mapping Function (direct, associative, set associative)
Replacement Algorithm (LRU, FIFO, LFU, Random)
Write Policy(Information integrity)(Write through, Write back)
Block Size (no definitive optimum value has been found)
Number of Caches (Single- or two-level, Unified or Split)
The Cache Efficiency is characterized by hit ratio. The hit ratio is a ratio of all hits in the cache to the number of CPU’s accesses to the memory.
 49)Draw up a block-diagram of Pentium processor and explain functions of its main nodes
49)Draw up a block-diagram of Pentium processor and explain functions of its main nodes 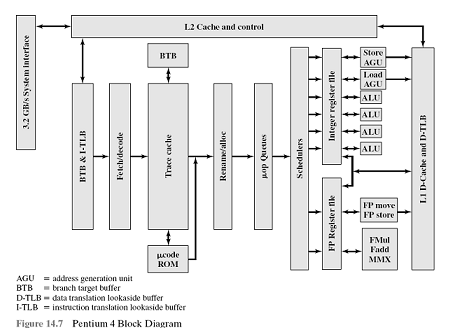
50) How is ensured the Data Cache Consistency?
Data Cache Consistency
To provide cache consistency the data cache supports a protocol MESI (modified/exclusive/ shared/invalid).
The data cache includes two status bits per tag, so each line can be in one of four states:
Modified: the line in the cache has been modified and it differs from that in the main memory, so it is available only in this cache.
Exclusive: The line in the cache is the same as that in the main memory and also is not present in any other cache.
Shared: The line in the cache is the same as that in the main memory and may be present in another cache.
Invalid: the line in the cache does not contain valid data.
59. a definition of Virtual Memory.. Usually only some parts of a program that are executed are first brought into the main memory; when a new part (segment) of a program is to be moved into the full memory, it must replace another segment already in the memory. In modern computers, the operating system moves programs and data automatically between the main memory and secondary storage. Techniques that automatically move program and data blocks into a physical main memory when they are required for execution are called virtual memory techniques. A special hardware unit, called Memory Management Unit (MMU), translates virtual address into physical address. When the desired data are in the main memory, these data are fetched as of the cache mechanism. If the data are not in the main memory, the MMU causes the operating system to bring the data into the memory from the disk. Transfer of data between the disk and the main memory is performed using the DMA.
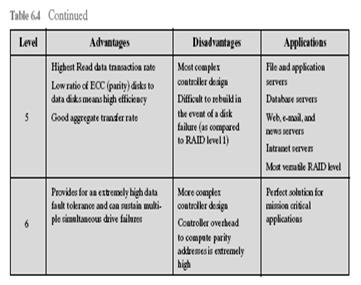
51)Why RAID 0 can not be considered as a true member of RAID family? Compare RAID 5 and RAID 6 (illust….

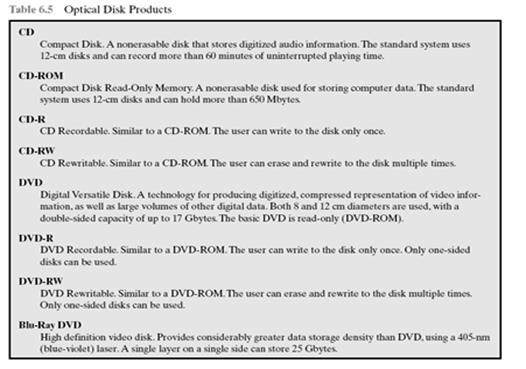
53. List the well-known Optical Disk products and describe their characteristics.
Дата добавления: 2015-10-26; просмотров: 123 | Нарушение авторских прав
| <== предыдущая страница | | | следующая страница ==> |
| Describe the mechanism of work with interrupts. | | | List the major characteristics of Disk System. |